Connecting state and local government leaders
Innovative security, a friendly (for real) cross-platform interface, and handy support for telework and BYOD could do a lot for public-sector organizations
Microsoft’s Windows 8 operating system could do a lot to change computing across all form factors. Make no mistake, this isn’t an incremental upgrade. Windows 8 is a sea change, in the way Windows 3.0 moved the world away from DOS.
Having spent the past couple months diving into every aspect of the new operating system, I can say that there will certainly be a bit of a learning curve, but probably less than most users expect. Once that hill is overcome, Windows 8 will offer so many advantages in terms of security and usability that it will be difficult to imagine how the world worked without it.
Public-sector workers especially should embrace these changes, because a stable and secure OS running across desktops, notebooks and tablets has been a missing component to most agencies’ build-out plans, leading to a bit of a hodgepodge of interfaces. For example, in the Commerce Department, the agency has about half of its systems running Microsoft Windows XP and half running Windows 7, which is about the same dispersal of systems worldwide. Getting every desktop and laptop onto the same page, and then extending that page to tablets would be a big help.
Windows 8 is part of Microsoft’s vision of a global operating system that is both platform and geographically independent. It looks exactly the same on a notebook, desktop, tablet or mobile device anywhere in the world. I learned how to use it on a desktop computer without a touch screen, and that made using the OS on a tablet like the Samsung Galaxy second nature without further training.
Most of the keyboard shortcuts from the desktop are simply replaced with hand gestures on the tablet, but everything looks and works exactly the same. Once the new OS proliferates, if you learn how to use Windows 8 on a notebook in France, you can run it on a desktop in the United States or a tablet in Japan. Changing the language options is easy to do, but almost not necessary since all devices will work the same way.
The new OS offers a lot of advantages for organizations. We’ve broken out five general advantages below, each of which include some other good features.
1. Bye, Bye BIOS
Beyond usability and the new interface, the biggest focus for Windows 8 is security, which we all know is the No. 1 concern for federal agencies. Here we find that new systems shipping with Windows 8 will benefit more than older ones being upgraded because of two key new features, with the biggest surprise being the elimination of the system BIOS.
The Basic Input/Output System was invented in 1976 and still acts as a bridge between hardware and most operating systems today. If you ever needed to hold down a function key during the boot process to type on that DOS-like screen in order to do things like changing your system clock, then you’ve been inside your BIOS. It works OK, but it’s also a very vulnerable part of the computing landscape and a favorite target of root kits, malware and modern viruses.
Windows 8 will work with BIOS, but it’s designed to function securely with the Unified Extensible Firmware Interface (UEFI), which should start replacing BIOS pretty soon after Windows 8 ships. In fact, to be considered Windows 8 certified, systems will need to use UEFI instead of BIOS.
The biggest security feature with UEFI is that it allows Windows 8 to reach out to the master boot record and check to ensure that everything is still in a pristine state, a process called Secure Boot. If any root kits or other malware have changed anything at all, or if the connection between Windows 8 and UEFI is somehow blocked, UEFI won’t allow a system to boot.
Some people might complain that this effectively makes it so that hardware designed for Windows 8 can’t ever run alternative operating systems, like Linux. In a sense this is true because if the connection between the Windows 8 OS and the UEFI is not made, the system won’t boot. However, Microsoft is allowing Linux companies to register so that their OSes can function the same way as Windows 8, and protect machines from boot-level malware. Red Hat Linux has already done that.
2. Boots kick out malware
The second major security upgrade with Windows 8 is Trusted Boot, which modifies a convenience technology found in Windows 7 to prevent accidental deletion of critical files. You might not know this, but if you’re running Windows 7 and you delete your Notepad program, it should come back after a few minutes. That’s because Notepad is considered essential, and a copy is stored in a secure part of your OS. If the system detects that it’s gone missing, it will copy it back over for you, which sort of idiot-proofs critical files.
Microsoft has taken that technology and modified it to work with critical .dll and system files during the boot process for Windows 8. The Trusted Boot process scans every file being loaded during the boot phase, including all the usual suspects targeted by malware. If any of the files have been replaced or modified in any way, the OS simply copies the actual file over the top of them from the secure area, and boots normally.
Trusted Boot and Secure Boot require new hardware, but there are several security features that will work just fine with existing computers being upgraded from an older OS. The most impressive is the early loading of anti-virus software, something that is sorely needed to combat malware.
A trick virus writers have used in recent years is to have their malware load its drivers and system commands before any anti-virus program. Then they can block AV from working, or even give false information to users. Windows 8 identifies legitimate anti-virus programs from known companies and loads their drivers first. And even if you don’t have an anti-virus program, Windows 8 ships with Windows Defender, which is of course flagged as a first-load program. So everyone with Windows 8 will have some form of virus protection, and it will be given priority over almost everything else on the system.
I was able to test this feature with a piece of malware from the GCN Lab’s virus vault that tries to pre-load before an AV program. The virus was successful in taking over a system running Windows XP even though it was protected by anti-virus software. But it failed in trying to use that same first-load trick to get around identical protection running under Windows 8. So this is a huge weapon in the fight against malware.
3. Encryption made easier
Specifically for feds, but good for anyone, Windows 8 has the option to fully encrypt an entire system using the BitLocker program. In the past, feds have been cool to embrace BitLocker because when pushing out an update to distributed systems, administrators did not have access to BitLocker-protected computers. What would happen is that the encrypted system would wake up and ask for the security key, but not install any patches or updates until that key was entered locally. Then when it was entered, the user, who was just coming into work, had to wait for the patch process to complete.
Windows 8 solves this problem by giving access to BitLocker-protected systems if a variety of conditions are met. A system must be plugged into its home and trusted network with a cable — wireless does not count — and then the administrator can wake it up and apply patches without local intervention. This could make BitLocker far more attractive in enterprise environments.
Where BitLocker protects entire drives, Windows 8 also improves security on individual files by adding an extra layer to Dynamic Access Control lists, which track permissions across a network, and are notoriously difficult to manage in large groups. An administrator can use common language to create an extra gateway to help plug holes that develop in the DAC list. For example, adding “If User.country = US, allow Read/Write” would be a way some organizations could make sure that each user is only reading a file if they are stationed within the United States, according to their Active Directory listing. This extra check happens before the DAC is even accessed, so if a user is from China in this example, the system doesn’t even bother to check the DAC. They are simply rejected and not allowed to read a protected file.
4. Keys to working remotely
The final major upgrade for Windows 8 in terms of security is that all copies of Windows 8 will support Windows to Go. That basically means that Windows 8 can be installed on a flash drive. Then when you plug the flash drive into any computer, you are able to work from the secure OS stored there and ignore whatever’s on the host computer you happen to be using.
This would allow feds and other government employees to work securely from a public terminal inside a mall if necessary, and would also prevent the loss of data if a notebook or tablet is stolen, since all the real data and even the OS is sitting on a secure key drive. It would allow feds to work from home and enable telework, bring your own device programs and continuity of operations plans.
There are some restrictions. Key drives must be certified as USB 3. You can use a USB 2 port on a host system, but the drive itself must be USB 3. The portable drive must also report itself as a fixed drive to the OS, something only a few do right now. Finally, you also need to purchase a number of Software Assurance Licenses from Microsoft, one for each drive you want to use, which gives you permission to use Windows To Go.
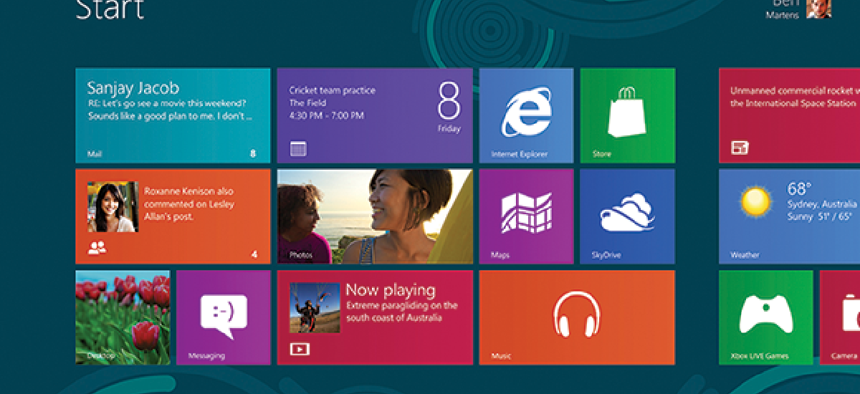
5. Friendly interface (really)
Beyond whether the new OS will be secure, probably the biggest fear people have is about the interface. Potential users are worried that their desktop computers, without touch screens for the most part, are being forced to boot into what looks like a tablet interface. I admit this was a concern when I started my testing. The old nightmare of going to class in your underwear could be replaced with showing up for work and suddenly not knowing how to use your computer. But trust me, this won’t be a problem.
The main boot screen is both incredibly powerful and easy to use. Every program installed on the system has an associated icon on the main screen. Clicking, with your finger or a mouse, depending on the device, runs the program. If you would like to get rid of a program, you simply uninstall the icon and that takes the entire thing away.
So the problem of eliminating shortcuts and leaving the actual program behind no longer exists. That should even reduce the bloatware that ships with some manufacturer’s systems, because it’s easy to see and can be eliminated in seconds by users of any skill level.
There is also a cheat with the new interface. If you really don’t like the point and click simplicity of Windows 8, you can hit your Windows key on your keyboard. That brings up the more classic view, and looks likes a Windows 7 desktop. And the Windows 7 desktop is also represented as an icon on the new main screen, so you can also click to get it there. Internally, most of the programs look and act the same as before. At most, a user might need an hour of training to learn the new interface, though they will probably catch on much more quickly than that.
Once you get used to the look of your new working environment, it’s easy to have it completely duplicated across all notebooks, desktops and tablets that you associate with yourself, so you can truly take your home screens with you anywhere. Or, an agency can create a perfect working space with all the programs users need, and then replicate that so everyone has access to the exact same configuration regardless of platform. Desktop, tablet and notebook users will all see the same screens, which is not only easier for users, but should take a huge load off of the tech support staff.
We don’t know if Microsoft’s vision of a globally used operating system will ultimately come to fruition, but feds don’t need that to happen in order to start taking advantage of Windows 8 right away. The new OS offers some incredible and innovative security features along with an easy-to-use-package that can be duplicated across almost every device in an entire agency. So there’s a lot to love about Windows 8, and really no reason to fear it.
It easily earns a GCN Lab Reviewer’s Choice designation, and our highest recommendation.