Connecting state and local government leaders
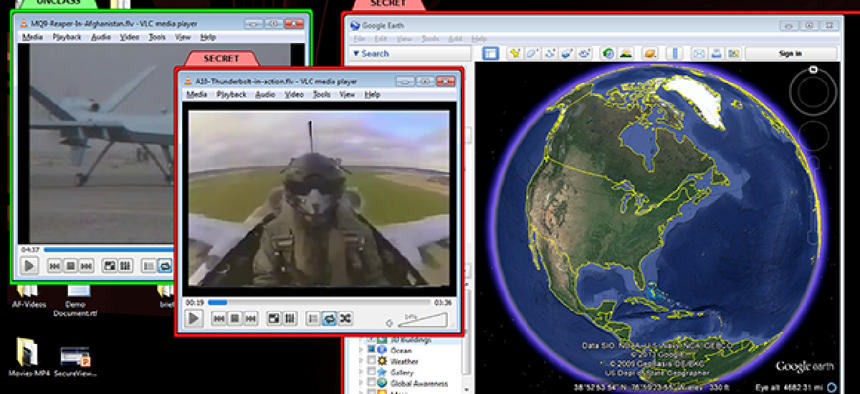
Developed by the Air Force Research Lab, Citrix and Intel, the system puts feeds from multiple networks on the same screen but prevents any data from being moved from one place to another.
“Connecting the dots” has become an increasingly public and controversial practice, as recent headlines will attest, but it has always been a primary goal of the intelligence community, and it got more complex after the terror attacks of Sept. 11, 2001.
When the 9/11 Commission highlighted the critical importance of collaboration between intelligence-gathering agencies, it still insisted that, for security reasons, the information feeds analysts received from different networks remain completely separate from each other.
At first, that meant analysts needed a dedicated stand-alone computer, monitor and keyboard for each feed they worked with. Secure KVM switches began to pare the desktop clutter down a bit, but with 17 different networks in the intelligence community, analysts needed several separate, secure computers just for basic functionality.
While it's unlikely that individual analysts would need access to every single network, John Woodruff, program manager of the Air Force Research Laboratory’s Cross Domain Solutions, Operations and Innovations team, has seen some complex setups. "It was not unusual at all to find an analyst with six to eight computers on his desk, with each one sitting on a different network," he said.
The solution involved more than decluttering desktops; it had to meet seemingly conflicting security and performance requirements. It had to tie all the networks into a single computer, but under no circumstances could data on any one network jump to another. And the solution had to support high-performance applications like video streaming without degrading the performance of the host agency’s network. Oh, and did I mention that it also had to be able to be configured for individual analysts within four hours?
After six months of testing, Woodruff and the AFRL team found a solution. Working with Citrix Systems and Intel, they came up with a security plan based on the bare metal hypervisor platform, which was able to handle high-performance workloads and graphically intense applications.
To create the program, dubbed SecureView, AFRL took Citrix's XenClient and modified it into XenClient XT so that it delivers the “client-side virtualization of XenClient in a multilevel secure local virtual desktop solution with the highest levels of isolation and security,” according to Citrix.
This modification required setting up a trusted boot process inside dom0 (“domain zero,” the first domain created) of the hypervisor. The Xen hypervisor, which runs the virtual machines, can then boot from a secure state. The network stack was also moved into a separate virtual machine, so that it would act like any other operating system or network that the hypervisor is responsible for – ensuring that no data can be sent to it, or leak from it, to any other network. Finally, SELinux was added to dom0 with a custom set of policies to harden the operating system even further.
SecureView will run on any system that supports Intel vPro technology. It also supports almost every operating system, including all flavors of Windows and Linux. Dell and Hewlett-Packard provided AFRL with access to their BIOS and firmware while the platform was being tested to help make it more secure. And the National Security Agency, which deals extensively with intell gathering and would likely be the biggest user on SecureView, collaborated throughout the creation process.
I was invited to Citrix's Bethesda, Md., headquarters to meet with Woodruff and to test the security and performance of a system running Version 2.0 of SecureView. I was surprised to find that the test unit was actually a notebook, with four different feeds streaming on it.
The first line of defense, and why SecureView would be a good solution even for users with only a single network feed, is that it uses a trusted boot process. When XenClient XT is installed, the system’s configurations are measured at their baseline state. Those measurements are stored in the system's Trusted Platform Module chip. Intel's Trusted Execution Technology measures the OS configurations each time it's booted to ensure nothing has been altered. The new measurements are used to unlock the encryption keys, and only if they match the baseline will any system powering SecureView even boot. Thus, any modifications made by programs or hackers will prevent the system from even turning on, shutting down trouble before it can even begin.
That's because SecureView takes over the computer’s local system, which is relegated to being just one of the feeds available and is unaware of, and unable to contact, any of the others.
The boot screen for SecureView shows the various network feeds the host machine can access, and they can be color coded to show their security levels. Each of the SecureView virtual machines — that is, each of the network feeds — is independent, though it may not look like that to a user.
The SecureView feature called Multiview allows multiple feeds to run on the same screen. I've never seen a security solution in the cross-domain area that could make that happen. In the demo, there were two live feeds, a movie and a 3D presentation running on different networks in the background while a user typed in a document on the simulated top-secret network in the forward-most window. So an analyst could be working on a top-secret report with a live CNN video feed in the corner of his screen with no danger of anything leaving its proper network. The secret is that it's all done with pixel replication. The feeds in the background are actually duplicates of the real thing, though even with live video, it was impossible to tell.
Data can't be copied from one feed to the desktop, and then into another network, something I thought might be possible. But remember that as part of hardening XenClient to XT, the dom0 was made into a virtual machine at the hypervisor level. So if a user tries to cut and paste something from one network to another, the data will never make it. It’s the same with trying to move something to the desktop, because essentially there is no longer a host system. There is, just a collection of virtual machines the user can work with; the host system — what a user would think of as the physical PC’s desktop — is just one of them. A user trying to move something to the desktop can switch over to the host OS, but the host OS has no idea that you copied data to the clipboard while working in another network, because it doesn't know that other network exists.
Woodruff showed that setting up a machine to use SecureView was also easy, well below the four-hour threshold originally tasked by the Office of the Director of National Intelligence. Essentially, system resources are assigned to each feed. "The upper limit to how many feeds you can have is dependent on your hardware," Woodruff said. "Typically we assign two to three gigabytes of memory per network. If you find that you need more, you can always go back and change that."
The cost for any government agency that wants to use SecureView is surprisingly inexpensive. I've seen secure KVM solutions that cost more, but offer a lot less. First, an agency needs to have a computer that supports Intel vPro — a Dell Optiplex 9010 or an HP Compaq Elite 8300 would work fine. Then the agency would have to buy a license to use Citrix's XenClient XT, which would run about $599 for a single license, though the company offers government and volume discounts. If an agency wants to set up SecureView itself, there are no additional costs. However, AFRL can set up the software for other agencies for a fee. AFRL also will maintain the software for as little as $25 per seat, depending on the quantity.
SecureView was surprisingly graceful given how secure it was. Switching from one network to the next was extremely easy, and even monitoring other networks was possible with Multiview, assuming there is a big enough screen. So far, SecureView has impressed a lot of government agencies as well. It got a favorable evaluation against the new NIST SP 800-53 Security Controls Catalog. It earned the Top Secret and Below Interoperability Authority to Operate certification from the Defense Intelligence Agency. And the new 2.0 version of the program is in the process of getting Secret and Below Interoperability certification, which would allow it to operate on DOD’s secure and unclassified networks (SIPRnet and NIPRnet) simultaneously.
Having tested and experienced countless security tools over the past 15 years, I can say that not only is SecureView actually rock-solid in terms of security, but it also has one of the most elegant interfaces I've encountered. I'm still dazzled by Multiview in that it would give an analyst all the functionality of multiple desktop computers without compromising security — and without the need for multiple systems cluttering up the workspace. Despite the participation of many government organizations and private companies in its creation, the end result with SecureView is a surprisingly inexpensive solution that perfectly matches the needs of the government security community. It's literally made by government for government.
NEXT STORY: Cell phones gear up to fight AIDS