News
Our News category at Global Current News provides fast, reliable coverage of breaking events and key developments worldwide, including in the United States. From political decisions and economic shifts to cultural milestones and scientific breakthroughs, our skilled journalists bring you the latest reports with precise, concise analysis. Stay informed and connected to the global conversation with up-to-the-minute updates.
Nationwide internet blackout imposed amid escalating unrest and mass demonstrations in Iran
Iran is currently experiencing one of the most unstable moments in its recent history, driven by a deep economic collapse...
Read moreDetailsMyanmar proceeds with another round of voting as armed conflict continues nationwide
Despite continued internal strife and condemnation from both opposition and international circles, Myanmar's ruling military has proceeded with the second...
Read moreDetailsInternational Court of Justice formally launches genocide proceedings over Myanmar’s treatment of the Rohingya
A major milestone occurred with the opening of hearings by the International Court of Justice (ICJ), regarding the allegations of...
Read moreDetailsIran’s president urges national unity as protests over economic collapse and repression intensify across the country
Political crises have plagued Iran in recent decades. With protests taking place throughout the country, Iran is facing one of...
Read moreDetailsDenmark signals a critical turning point in tensions with the United States over Greenland’s status
With a military threat looming large over Greenland, there are many questions about Denmark’s ability to protect its interests and/or...
Read moreDetailsNorth Korea conducts ballistic missile tests ahead of upcoming regional talks
Regional tensions increased after North Korea conducted several ballistic missile test firings, when regional representatives meet for important discussions. According...
Read moreDetailsNATO’s cohesion comes under strain as Trump suggests a possible choice between Greenland and Europe
At his January 8, 2026 press conference, President Trump mentioned the possibility of having to choose between Greenland and the...
Read moreDetailsChile’s Catholic bishops issue appeal for dialogue and stability in Venezuela
Recent events in Venezuela involving the kidnapping of President Nicolás Maduro by US forces continue to generate repercussions and impact...
Read moreDetailsIndia convenes international election summit with representatives from 42 nations
India is hosting an international election management conference. The conference brings 42 nations together to discuss ways to strengthen election...
Read moreDetailsAfrican Union Peace and Security Council reasserts Somalia’s sovereignty amid regional security concerns
At an African Union Ministerial Meeting for Peace & Security Council (PSC) on January 6, 2026, the African Union reaffirmed...
Read moreDetailsCanada eases visitor-visa rules, permitting stays of up to twelve months
Canada is famous for being a tourist destination that attracts people from all over the world, and in early 2026,...
Read moreDetailsUnited States plans broad withdrawal from multiple UN agencies and international organizations
As part of his "America First" agenda, President Donald Trump has announced plans to withdraw from a large number of...
Read moreDetailsVenezuela imposes nationwide state of emergency as political and economic crisis deepens
Things are getting worse in Venezuela every day. The interim government in Venezuela has declared an emergency as the political...
Read moreDetailsSaudi Arabia hosts the start of the 2026 Dakar Rally
In the automotive world, Saudi Arabia has once again become the center of attention, having been chosen to host the...
Read moreDetailsRights groups say at least 16 people died during a week of nationwide protests in Iran
Human rights organizations have confirmed that at least 16 individuals died as a result of a nationwide protest campaign that...
Read moreDetailsAustralia welcomes 2026 under tightened security measures following a recent terror incident
Beyond the traditions already known throughout Australia and the world, the arrival of 2026 occurred amidst a climate of caution,...
Read moreDetailsUnrest widens across Iran as protests intensify and at least six deaths are reported
As Iran's economy declines, it has experienced a large-scale protest movement — the biggest in decades. This protest movement is...
Read moreDetailsMalaysia introduces stricter hygiene licensing requirements for commercial businesses
In 2026, the Malaysian Government intends to implement a new system of hygiene licensing for all commercial establishments in Malaysia....
Read moreDetailsAPEC 2026 to convene in Shenzhen as China positions tech hub at center of regional diplomacy
The APEC 2026 summit will be held in Shenzhen, and this decision, in addition to being a diplomatic announcement, was...
Read moreDetailsGlobal initiative on disruptive technologies to launch in January 2026 to speed progress on the SDGs
We can expect a new worldwide initiative that will pioneer the use of new, disruptive technologies in 2026. The program...
Read moreDetailsColombia deploys troops to the border as tensions rise following Venezuela crisis
Last week, Venezuelan President Nicolás Maduro was captured and imprisoned following a US operation in the country, and the diplomatic...
Read moreDetailsFuel prices may be lower after QatarEnergy’s latest statement
On QatarEnergy's official announcement dated December 31, 2025, concerning Qatar's petrol prices for January 2026, it was stated that prices...
Read moreDetailsIter’s giant fusion reactor in southern France hits a major assembly milestone with vacuum chamber module 5
Inside a concrete pit near Cadarache, engineers have positioned ITER’s fifth vacuum vessel module—an ultra-precise step that brings the world’s...
Read moreDetailsChina’s two-second maglev burst to 700 km/h hints at what the next generation of trains could look like
A superconducting maglev test rig in China accelerated from 0 to 700 km/h in just two seconds on a 400-metre...
Read moreDetailsEconomic pressures fuel widening protests across multiple cities in Iran
Protests are erupting across dozens of cities in Iran as the country experiences the worst unrest it has seen since...
Read moreDetailsGoing a mile underground to run a nuclear reactor: why Deep Fission says rock pressure could replace giant domes
A US start-up is pushing an unusual idea for small nuclear power: drop a conventional pressurised-water reactor into a narrow...
Read moreDetailsUnder Norway’s North Sea, a 600‑meter‑deep desalination capsule could reshape how cities get drinking water in 2026
A submerged desalination project off Mongstad, Norway, plans to use deep-ocean pressure to push seawater through reverse-osmosis membranes—aiming to cut...
Read moreDetailsFrance ships a 500-tonne reactor vessel to Hinkley Point C as Britain’s new nuclear era takes shape
A 500-tonne reactor pressure vessel forged in eastern France is heading to Somerset, where it will become a central part...
Read moreDetailsAt 5,600 metres in the Kunlun mountains, China is using driverless trucks to unlock a €45 billion lead-zinc prize
In the thin air of Huoshaoyun—where cold, altitude and logistics make conventional mining punishing—China is leaning on autonomous haul trucks...
Read moreDetailsUnited States begins military action in Venezuela and detains President Nicolás Maduro
One of the biggest diplomatic and military crises of recent decades has just occurred between the United States and Venezuela....
Read moreDetailsDelcy Rodríguez takes office as Venezuela’s new leader as international tensions intensify
Delcy Rodríguez was sworn in as Venezuela's acting leader on January 4, 2026, marking a major change in Venezuela's political...
Read moreDetailsNorth Korea fires ballistic missiles ahead of South Korean president’s planned visit to China
Pyongyang launched multiple ballistic missiles into the East Sea on January 4 at 7:50 a.m., just hours before South Korean...
Read moreDetailsUnited States widens visa restrictions and raises immigration fees for travelers from 39 countries
The political landscape of the United States is facing some changes, especially the country's immigration policy, which is entering a...
Read moreDetailsBulgaria formally joins the euro area, becoming its 21st member
Beginning January 1, 2026, Bulgaria will start using the euro as its main currency, making it the 21st country to...
Read moreDetailsEurope begins phased deployment of the new Schengen entry–exit system at major airports
Recently, the European Union initiated the launch of a number of large-scale airports within the Schengen region to begin rolling...
Read moreDetailsDeadly blaze at a Swiss ski resort bar leaves at least 40 dead and more than 115 injured
According to reports from PEOPLE magazine, a fire that took place in the Swiss Le Constellation bar in Crans-Montana during...
Read moreDetailsLithuania introduces language requirement obliging foreign residents to serve the public in the national language
Lithuania has made an important decision regarding the use of its official language in the daily lives of its population....
Read moreDetailsUnited States rolls out broad new visa restrictions and raises travel-related fees
The United States is expected to begin 2026 within a comprehensive framework of travel and immigration reforms that will include...
Read moreDetailsScientists are stunned: 8 new spacecraft images reveal interstellar comet 3I ATLAS in such unsettling detail it doesn’t look real
The astronomical community is in a state of shock following the release of a new set of eight high-resolution spacecraft...
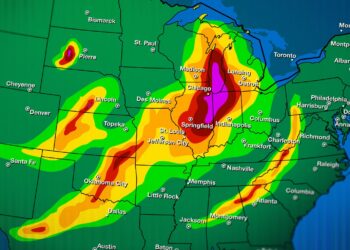
Read moreDetailsA historic early-season polar vortex shift is surging, and experts say its intensity is unmatched for January
Meteorologists are currently monitoring a massive atmospheric anomaly as a significant disruption of the polar vortex begins to take shape...
Read moreDetailsWTTC selects Valletta to host its 2026 global summit, highlighting sustainable tourism goals
The city of Valletta, in Malta, has been chosen by the World Travel & Tourism Council (WTTC) to host the...
Read moreDetailsSix minutes of darkness: Get ready for the longest eclipse of the century that will turn day into night
Imagine that, in the middle of lunch, the sky begins to take on a metallic tone, the birds fall silent,...
Read moreDetailsColombia to host first global summit dedicated to phasing out fossil fuels in April 2026
Colombia has made climate diplomacy history by becoming the first nation to organize an international summit on the global phase-out...
Read moreDetailsIOM warns looming budget cuts could jeopardize core programs in 2026
The International Organization for Migration (IOM) has issued a worrying warning about the international migration scenario, which concerns a forecast...
Read moreDetailsUNCTAD to host 2026 investment forum in Qatar aimed at addressing global economic fragmentation
The UNCTAD has disclosed details of its upcoming 9th World Investment Forum (WIF), which will occur in Doha, Qatar, in...
Read moreDetailsG7 leaders to convene in Évian-les-Bains in June 2026 as economic and climate pressures intensify
From June 14th to 16th, 2026, the French city of Évian-les-Bains will be in the global spotlight due to the...
Read moreDetailsWTO warns rising U.S.–China trade friction could intensify heading into 2026
With the approach of 2026, the World Trade Organization has issued a dire prediction to the globe. The prediction warns...
Read moreDetailsNATO selects Ankara to host its 2026 summit amid heightened focus on the eastern frontier
NATO's 2026 summit will be held in Ankara for the first time, which, in addition to raising the level of...
Read moreDetailsRiyadh prepares to host global defense exhibition in February 2026 amid growing strategic ambitions
Saudi Arabia will hold the third installment of the World Defence Show (WDS), to be held in Riyadh from the...
Read moreDetailsIOM cautions that deep budget cuts could disrupt key migrant programs in 2026
The International Organisation for Migration (IOM) has already issued a warning that also serves as a cause for concern for...
Read moreDetails