Automotive
Our Automotive section delivers authoritative coverage of the dynamic forces reshaping mobility—from electric vehicle rollouts and autonomous driving regulations to supply chain disruptions and high-profile safety recalls. We analyze market trends, legislative changes, and technological innovations—such as connected-car platforms and next-generation charging infrastructure—through concise, investigative reports. Stay informed on the strategic developments and emerging solutions steering the future of transportation.
Xiaomi offers tax rebates for early EV buyers with 2026 delivery orders
China's electric vehicle market just got interesting. Xiaomi announced Friday it'll be covering the increase in tax for those who...
Read moreDetailsEvonik expands in Asia with new aluminum specialties facility in Japan for EV and coatings markets
Evonik, the German chemical giant, has just commissioned its first fumed alumina plant in Japan, evidencing a strategic change in...
Read moreDetailsJapan’s trade data show car exports climbing to Asia but dropping in the U.S.
Japan's automobile sector is bracing for an imminent geographical shift, with September trade figures showing opposite fates of different markets...
Read moreDetailsIndonesia to launch domestic car production within three years, says Prabowo
On the first anniversary of his inauguration, President Prabowo Subianto declared an ambitious car independence program. Indonesia stands to recover...
Read moreDetailsJeep relocates Compass production to Illinois to sidestep trade tariffs
Stellantis is taking a strategic manufacturing move that will disrupt the North American automobile sector. The automobile business has turned...
Read moreDetailsStellantis to increase U.S. production by 50% in $13 billion expansion plan
Stellantis NV announced a record investment in history, worth $13 billion in the United States market over the next four...
Read moreDetailsJapan cautions Vietnam on job losses as Hanoi’s motorbike ban impacts Honda
Diplomatic tensions increase as Japan's government takes action to protect its motorcycle manufacturers from Vietnam's green policies. The Hanoi-based Japanese...
Read moreDetailsMercedes-Benz becomes first automaker to commit to global fossil-carbon-free program
Mercedes-Benz becomes history of automobiles when it joins the Renewable Carbon Initiative as a member, pioneering fossil-free car manufacturing through...
Read moreDetailsWeRide gains approval in France for Level 4 autonomous vehicle testing
Another historic moment of autonomous mobility in the world is the entry of WeRide in Europe. The Chinese autonomous technology...
Read moreDetailsJeep shifts North American Compass production to Illinois to avoid tariffs
Stellantis has revealed that it would be shifting Jeep Compass production from its Brampton, Ontario, plant to Illinois and has...
Read moreDetailsAbu Dhabi to build new EV export hub through Stellantis partnership
Abu Dhabi is staking out its position as the Middle East's automotive powerhouse through a ground-breaking alliance with global manufacturing...
Read moreDetailsAutomakers warn of electric vehicle slowdown as federal credit phase-out takes hold
The federal electric vehicle tax credit, which was $7,500 formally, expired on September 30, 2025, making it part of the...
Read moreDetailsJaguar Land Rover resumes factory lines after major cyberattack disruption
Jaguar Land Rover has declared to start manufacturing again in phases after over one month of suspension of production due...
Read moreDetailsEuropean Commission launches ‘AI-first’ initiative to accelerate self-driving vehicle adoption
As competitive pressures from overseas providers of high-appeal autonomous car services grow, European leaders are scrambling to secure their continent's...
Read moreDetailsUS auto buyers defy tariffs and inflation, boosting Q3 sales
Against the backdrop of economic headwinds such as tariffs and inflation, American consumers persevered to create strong third-quarter automobile sales,...
Read moreDetailsGM abandons effort to extend EV tax credit past official cutoff date
General Motors has suddenly reversed its decision on its extension to continue offering the $7,500 federal EV tax credit after...
Read moreDetailsTesla’s budget Model Y struggles as competition in Europe intensifies
After the federal EV tax credit of $7500 per car had expired, Tesla also introduced less affordable Standard models of...
Read moreDetailsNissan to end vehicle production at Oppama plant by 2028
Nissan Motor said its vehicle manufacturing at the historic Oppama plant had been decided to end at the end of...
Read moreDetailsTata overtakes rivals to become India’s No.2 carmaker ahead of October launches
India Tata Motors has regained second place in the Indian passenger vehicle market, overtaking Mahindra and Hyundai in September 2025...
Read moreDetailsChinese EV and autonomous driving firms expand road tests and R&D hubs in Europe
The Chinese EV and self-driving technology firms are speeding up their European growth because the limitations in the U.S. market...
Read moreDetailsDanish auto sales inch up in 2025 as Tesla falters
In 2025, after rolling out a facelift to the Model Y in the European market, Tesla's sales recorded mediocre sales,...
Read moreDetailsGet or renew a Philadelphia residential parking permit online (PPA)
City of Brotherly Love residents have access to their Philadelphia residential parking permit online through the streamlined PPA digital platform...
Read moreDetailsHonda reports August Japan output down to 44,586 vehicles
In August 2025, Honda Motor stated that fewer automobiles would be produced in Japan and their number would be reduced...
Read moreDetailsUse a digital copy of vehicle registration in Tennessee (LESTER Act): How to access and show it
Volunteer State drivers now can legally show a digital copy of vehicle registration in Tennessee during traffic stops, thanks to the groundbreaking...
Read moreDetailsBMW debuts Neue Klasse iX3 electric SUV at Munich show
BMW has unveiled its revolutionary iX3 electric SUV at IAA Mobility in Munich as the first automobile suitable for series...
Read moreDetailsVolvo EX30 debuts in India at ₹39.99 lakh; prices to rise after Oct 19
Volvo India introduced its cheapest electric SUV, the EX30, at an introductory price of ₹39.99 lakh to first adopters. The...
Read moreDetailsChina preps tighter rules, support for auto market
China announced detailed policies to stabilize the automotive industry with more stringent policies and supportive policies, aiming at achieving 32.3...
Read moreDetailsTransfer a Utah vehicle title online with UPP (person-to-person, instant temp permit)
The residents of the Beehive State are now able to complete the procedure to transfer a Utah vehicle title entirely online...
Read moreDetailsXpeng recalls 47,490 P7+ sedans in China for steering defect
Xpeng, a Chinese electric motor manufacturing firm, recalled large quantities of 47,490 Chinese electric sedans, the P7+, in a grave...
Read moreDetailsApply for a Boston resident parking permit with the new online portal
Those who live in Baltimore can receive their Boston resident parking permit now through an updated digital system that does...
Read moreDetailsBYD leads Chinese EVs eroding Japan’s market edge in Southeast Asia
The introduction of electric vehicles at a very rapid speed by the Chinese automobile manufacturers, headed by BYD, are literally...
Read moreDetailsBuy or renew a Chicago city vehicle sticker online and add residential zone parking
The residents of Windy City can order their Chicago city vehicle sticker online conveniently through the EzBuy platform, without stepping...
Read moreDetailsEU BEV share steady at 15.8% through August
The market share of European battery electric vehicles (EU BEV) was unchanged at 15.8% up to August 2025 and has...
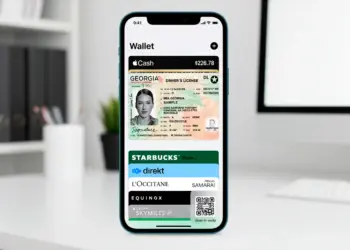
Read moreDetailsAdd your Georgia digital ID to Apple, Google, or Samsung Wallet
Using the major wallet applications, residents of the Peach State can now store their Georgia digital ID on smartphones to...
Read moreDetailsTesla sales slide in EU despite BEV market growth
The sales of Tesla in the European Union dropped by 37 percent annually in August, the second month in a...
Read moreDetailsApply for a Texas disabled parking placard or plates through your county tax office
The citizens of the Lone Star State who need convenient parking services are required to receive their Texas disabled parking...
Read moreDetailsJapan Engine clears first ammonia-fueled engine test
Japan Engine Corporation (J-ENG) has already attracted a world-first fully-functional ammonia-powered engine, and it is a breakthrough in decarbonization efforts...
Read moreDetailsIAA Mobility 2025 unveils bold EV concepts from Europe’s automakers
Munich IAA Mobility 2025 revealed the European transformation in the automotive industry with daring designs of electric vehicles and fresh...
Read moreDetailsHow to get a Massachusetts MOR-EV voucher before you buy so you can redeem at point of sale
Bay state cars are able to acquire guaranteed electric vehicle discounts via the Massachusetts MOR-EV voucher procurement procedure within the...
Read moreDetailsBMW Neue Klasse iX3 debuts in New York Sept. 21
On September 21, 2020, BMW opened the North American debut of the revolutionary BMW Neue Klasse iX3 at Bathhouse studios...
Read moreDetailsHow to apply for LA Metro LIFE low-income fare program with 2025 auto-benefit update
The Los Angeles County LA Metro LIFE initiative transformed the situation with the launch of payment techniques for the impoverished...
Read moreDetailsMercedes-AMG E53 wagon launches in US at $94,500
Mercedes-AMG has released the prices of its new 2026 E53 wagon, which will be sold in the US dealerships in...
Read moreDetailsHow to renew a California disabled person parking placard entirely online
Golden State residents can now complete their California disabled person parking placard renewal process entirely through digital channels without visiting DMV offices...
Read moreDetailsHyundai pulls Palisade SUVs for faulty seat-belt latches, regulator filing shows
Hyundai Motor America is also recalling almost 570,000 Palisade SUV models 2020-2025 because of faulty seat belt buckles that cannot...
Read moreDetailsHow to check your car for safety recalls by VIN and schedule a free repair
The owners are able to ensure their families by performing periodic checks of the safety recalls by VIN over the...
Read moreDetailsClaim New Jersey Charge Up 2025 EV rebate at the dealership
With the streamlined point-of-sale rebate obstacle in the New Jersey Charge Up calculation, electric vehicle customers can currently increase promptly...
Read moreDetailsNissan teases AI-Lidar ProPilot| due by 2027
Revolutionary next-generation ProPilot autonomous driving system with advanced AI technology and LiDAR sensors, planned to be launched in Japan in...
Read moreDetailsEnroll in Bay Area Clipper START: How to apply and activate your card
California's most comprehensive transit discount program, Bay Area Clipper START, revolutionizes affordable transportation access for working adults throughout the nine-county region....
Read moreDetailsPorsche unveils 11kW wireless charging for Cayenne EV
Porsche has also shown a revolutionary wireless charging system for its future all-electric Cayenne at the IAA Mobility in Munich....
Read moreDetailsGet Honolulu low-income transit fare (HOLO): How to apply, verify income, and load your card
The Honolulu low-income transit fare program, which the City and County runs, can provide Oahu residents with great savings if...
Read moreDetails