Cybersecurity
ChatGPT Plus
UN cybercrime treaty talks in Hanoi ignite global clash over privacy and state control
World diplomats have converged on Vietnam's capital for what is shaping up to be the most contentious cybercrime treaty in...
Read moreDetailsKyndryl joins EU initiative to strengthen cybersecurity training and workforce skills
Kyndryl, the tech titan, makes an unprecedented European cybersecurity training commitment in an unprecedented partnership. The company commits to sweeping...
Read moreDetailsEU develops independent security database after U.S. system dependency revealed
European cyberspace is witnessing a paradigm shift as governments are grappling with the reality that the cyber framework in their...
Read moreDetailsSenate bill aims to renew cyber cooperation and expand defense measures
A bipartisan Senate bill endeavor is designed to reinstate important protections that recently lapsed for cybersecurity, which is vital for...
Read moreDetailsCISA flags major cyber risk after hackers steal F5 source code
As elite attackers breach critical network systems, U.S. cybersecurity officials urge immediate action. Following a devastating hack that has left...
Read moreDetailsF5 Networks breach raises alarms over critical infrastructure and software supply chains
Sophisticated country-state cyber attack against F5 Networks reveals weaknesses in critical infrastructure systems employed across the globe by government organizations...
Read moreDetailsEuropean data brokers raise security alarms abroad
The European data brokers' industry is now a concern for the rest of the world. Once considered a largely consumer...
Read moreDetailsNation-state hackers behind F5 breach; source code likely stolen
F5 Networks has revealed a terrible cyberattack that gave highly privileged threat actors permanent access to critical systems and source...
Read moreDetailsAirports shut down after cyberattack hits core software system
The entire global aviation industry came to a standstill as the hackers attacked a vital part of the infrastructure that...
Read moreDetailsKey US cybersecurity law lapses during shutdown, halting information sharing programs
The Cybersecurity Information Sharing Act of 2015 officially expired on September 30, 2025, removing legally guaranteed protections for organizations sharing...
Read moreDetailsSecurity experts warn 50,000 Cisco firewalls remain exposed without urgent patch
The security researchers have detected close to 50,000 Cisco firewall devices all over the globe, and they are still susceptible...
Read moreDetailsCl0p hackers exploit Oracle vulnerability to hit multiple companies
Internet attackers have simply snatched off what keeps security specialists on their feet. The Cl0p ransomware gang found a mega-sized...
Read moreDetailsMajor U.S. cybersecurity law lapses as government shutdown fight drags on
Critical cybersecurity protections for American businesses have disappeared in the throes of congressional gridlock - leaving the private companies vulnerable...
Read moreDetailsExperts warn US cybersecurity cuts leave Pentagon and federal agencies at risk
Cybersecurity experts are mounting desperate warnings over proposed federal budget cuts that would jeopardize national security defenses in the Pentagon...
Read moreDetailsZero trust security delivers benefits, but AI-driven defenses still lag
The first, deeper world cybersecurity report released by DXC Technology and Microsoft demonstrates that, despite the fact that 83% of...
Read moreDetailsOracle warns customers of extortion attempts linked to hacker campaign
Oracle has sent immediate notifications to clients concerning attempts of extortion still underway after a zero-day sneak attack was determined...
Read moreDetailsUse Google passkeys (and move toward password-free sign-in) on your account
The future of authentication is coming with the use of Google passkeys to substitute conventional passwords with biometric authentication, which...
Read moreDetailsOoredoo expands cybersecurity offerings across Middle Eastern markets
Ooredoo Group has introduced the delivery of higher-level cybersecurity services in its global markets in collaboration with Innovatix Systems LLC....
Read moreDetailsGet an IRS Identity Protection PIN for 2025 to block tax-refund fraud
American taxpayers are now proactive in protecting their tax returns by receiving an IRS Identity Protection PIN from the agency's improved online...
Read moreDetailsUK cyber agency warns of malware wave targeting outdated Cisco gear
The National Cyber Security Centre of the UK has also raised an alarm based on complex malware campaigns on old,...
Read moreDetailsHow to prepare for Microsoft mandatory MFA enforcement
Time's running out! Microsoft mandatory MFA enforcement is bulldozing its way into organizations across the globe, and the October 2025...
Read moreDetailsAccenture strikes ~A$1B takeover of Australia’s CyberCX in cybersecurity consolidation push
As a part of the largest ever cybersecurity acquisition in the company, Accenture, one of the largest consulting companies in...
Read moreDetailsHow to send fully encrypted Gmail to outside recipients
Have you ever wondered whether it is possible to send fully encrypted Gmail messages that not even Google could intrude...
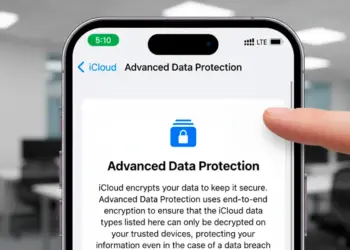
Read moreDetailsEnable Apple Advanced Data Protection for iCloud
Apple users can now activate Apple Advanced Data Protection for iCloud to secure their most sensitive data with military-grade encryption that...
Read moreDetailsChina-linked hackers exploited Ivanti flaws to hit European media firm, SentinelOne says
SentinelOne exposed the failure of a global hacking campaign orchestrated by hackers with links to China and attempted on SentinelOne...
Read moreDetailsTurn on iPhone Stolen Device Protection to block passcode hijacks
The latest iOS 17.3 security change allows Apple users to activate iPhone stolen device protection and ensures that thieves do not...
Read moreDetailsRiyadh cybersecurity forum unveils joint plans to strengthen online defenses
The fifth Global Cybersecurity Forum (GCF) kicked off on Wednesday in Riyadh, hosting significant plans to scale collaborative expertise in...
Read moreDetailsNew Zealand cyber agency reports over 1,300 Q2 incidents
New Zealand's National Cyber Security Centre has tracked 1,315 cybersecurity incidents over the second quarter of 2025, 3% less than...
Read moreDetailsEnisa 2025 threat report highlights surge in supply-chain hacks and zero-days
European Union Agency on Cybersecurity has released its inaugural successful report on Threat Landscape 2025, which reviews 4,875 successful incidents...
Read moreDetailsIndia’s CERT-In flags new flaws in enterprise software
The cybersecurity monitoring body of India, the CERT-In, has generated high-severity warnings regarding vulnerabilities in Google Chrome and Microsoft products...
Read moreDetailsRansomware blamed for airport check-in chaos across Europe
A ransomware attack on check-in systems at Collins Aerospace has led to massive disruptions in major European airports since Friday,...
Read moreDetailsAWS confirms New Zealand launch, promising data residency and lower latency
Amazon Web Services has now formally announced the deployment of its AWS Asia Pacific (New Zealand) Region which will bring...
Read moreDetailsHardbit ransomware tied to Europe airport disruption
Airports across Europe experienced a lot of disorder shortly after cybersecurity specialists detected HardBit ransomware as the culprit in large-scale...
Read moreDetailsRansomware tied to recent airport disruptions, probes ongoing
The airports of Europe suffered huge inconveniences when Collins Aerospace's MUSE platform was infected by HardBit ransomware on September 19,...
Read moreDetailsUK police arrest suspect in ransomware airport attack
The incident involving the ransomware attack that affected European airports over the weekend, resulting in massive flight delays and cancellations,...
Read moreDetailsJLR factories remain idle amid UK cyber probe
Jaguar Land Rover has given an extension of its production until October 1, 2025, after a complex cyberattack that caused...
Read moreDetailsGoogle fixes Chrome zero-day CVE-2025-10585
Google has released emergency security patches to address CVE-2025-10585, a high-severity zero-day bug in the V8 JavaScript engine of Chrome...
Read moreDetailsResearchers warn of Apple ImageIO zero-day exploits
Apple has also issued an emergency security release to address a major Apple ImageIO zero-day vulnerability in its framework that...
Read moreDetailsTurn off Chrome ad topics and other Privacy Sandbox ad settings
The new advertisement system adopted by Google requires consumers to manually turn off Chrome ad topics in case they want...
Read moreDetailsCISA outlines malware tied to Ivanti flaws and publishes detection guidance
The Cybersecurity and Infrastructure Security Agency published detailed recommendations on two malware versions that targeted the Ivanti Endpoint Manager Mobile....
Read moreDetailsNew GoAnywhere flaw heightens supply-chain attack risks
Security experts are raising an alarm about the possibility of supply-chain attacks, particularly by hackers on GoAnywhere MFT, a popular...
Read moreDetailsSamsung patches Android zero-day exploited in attacks
Samsung has scampered to fix a severe zero-day vulnerability, which was proactively utilized by creative attackers who aim the Android...
Read moreDetailsMicrosoft patch fixes 80+ flaws, two zero-days
Microsoft has also offered security patches for 81 categories of vulnerabilities in September 2025 and on Patch Tuesday, two of...
Read moreDetailsHow to create and manage passkeys on Windows 11
The most recent security innovation by Microsoft allows you to generate passkeys on Windows 11, which do not use passwords...
Read moreDetailsApple issues security updates for iPhone, iPad, Mac
Apple has also issued system security releases throughout the device ecosystem, fixing 27 bugs in iOS 26 and iPadOS 26,...
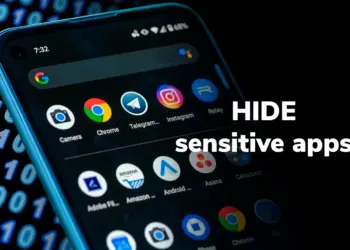
Read moreDetailsSet up private space on Android to hide sensitive apps
Ever wanted to set up private space on Android without anybody knowing? Android 15 is the first operating system to...
Read moreDetailsSamsung fixes zero-day flaw targeting Android devices
After being alerted to the vulnerability by WhatsApp and the security teams at Meta, Samsung has scurried to fix a...
Read moreDetailsAI speeds cybercrime while strengthening defenses
The adoption of artificial intelligence (AI) has unleashed apocalyptic dual-edged sword throughout the cybersecurity community, at once enabling cybercriminals to...
Read moreDetailsSamsung fixes Android zero-day hitting Galaxy devices
In an advertisement of sensational disclosure that has stirred sensations in the cybersecurity circle, Samsung has hurried out to mend...
Read moreDetailsMicrosoft Patch Tuesday fixes 86 flaws, two zero-days
Microsoft has already issued security patches to cover 81 vulnerabilities affecting Windows, Office, SQL Server, and other Microsoft-based products, including...
Read moreDetails